Introduction to DCIPP and RHEL 8
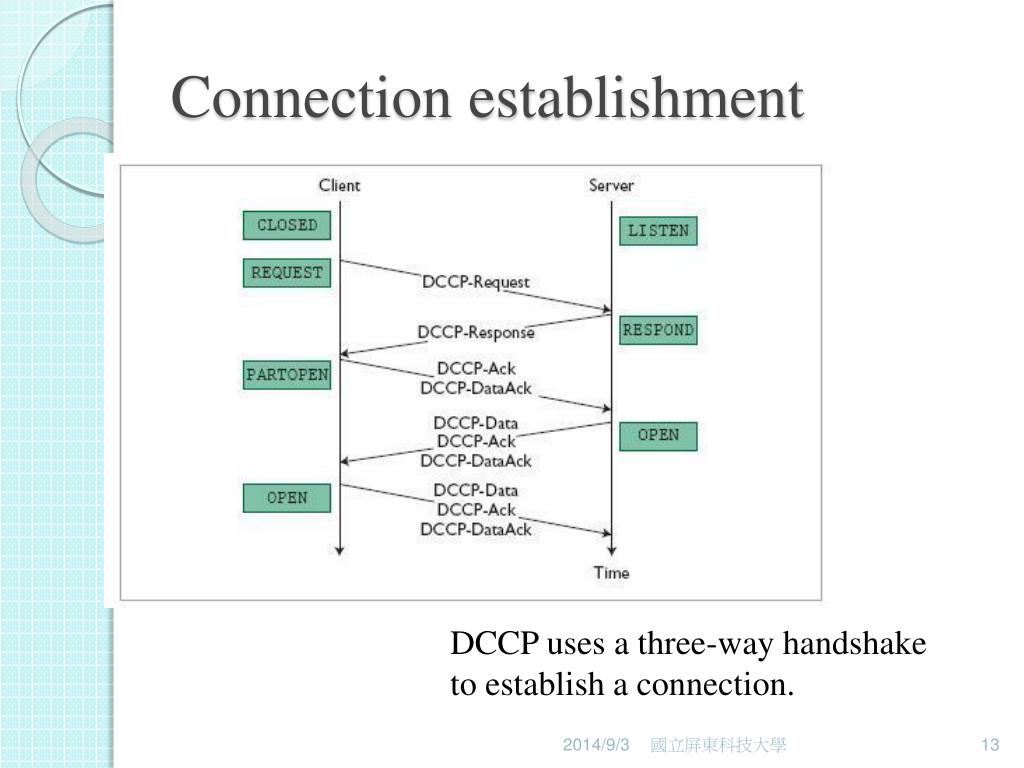
Data Center Internet Protocol (DCIPP) is a protocol designed to improve the efficiency and reliability of network communication in data centers. It aims to optimize the flow of data between servers and network devices, reducing latency and improving overall performance. DCIPP is often used in environments with high-bandwidth demands and tight latency requirements, like those found in cloud computing and enterprise data centers.
DCIPP plays a crucial role in the networking infrastructure of RHEL 8 systems, enabling fast and reliable communication between machines. Proper configuration and utilization of DCIPP can lead to enhanced network performance, especially in scenarios with many simultaneous connections and large data transfers. However, it’s important to understand the potential impacts of disabling this protocol.
DCIPP in RHEL 8 Networking, How to disable dccp in rhel 8
RHEL 8, like other modern Linux distributions, integrates DCIPP into its networking stack. This integration allows for optimized network traffic management, potentially enhancing throughput and reducing latency. The protocol contributes to the overall efficiency of the system by providing features such as packet prioritization and congestion control.
Potential Impacts of Disabling DCIPP
Disabling DCIPP on an RHEL 8 system can have several consequences. In some cases, network performance might degrade, particularly in high-traffic situations. This could manifest as slower data transfer speeds, increased latency, or more frequent packet loss. Conversely, in low-traffic scenarios, disabling DCIPP might not significantly impact the network performance. The impact depends heavily on the specific network configuration and workload.
Scenarios Requiring DCIPP Disablement
Disabling DCIPP might be necessary in specific scenarios. For instance, if a network administrator is troubleshooting a network issue, disabling DCIPP can help isolate the problem. Additionally, in some environments, DCIPP might interfere with other network protocols or security measures. Compatibility issues with specific network hardware or software components could also necessitate disabling the protocol.
Table: DCIPP Feature, Description, and Impact on RHEL 8
| DCIPP Feature | Description | Impact on RHEL 8 |
|---|---|---|
| Packet Prioritization | DCIPP prioritizes packets based on importance and urgency. | Disabling may result in reduced performance for time-sensitive applications. |
| Congestion Control | DCIPP helps manage network congestion by regulating traffic flow. | Disabling may lead to network instability under heavy loads. |
| Optimized Routing | DCIPP can optimize routing paths for faster data delivery. | Disabling might cause longer routing times and reduced throughput. |
| Security Features | DCIPP might include features like authentication and encryption. | Disabling may expose the system to security risks. |
Methods for Disabling DCIPP
Disabling Data Center Bridging Protocol (DCIPP) on Red Hat Enterprise Linux 8 (RHEL 8) can be crucial for network optimization or troubleshooting. Proper configuration prevents unnecessary traffic, ensuring optimal performance and security. This section details various methods for disabling DCIPP, focusing on the flexibility offered by `firewalld` and `iptables`.
Firewalld Configuration for DCIPP
The `firewalld` service in RHEL 8 provides a user-friendly interface for managing network rules, including those related to DCIPP. This method offers a comprehensive approach for controlling network traffic, enhancing security, and troubleshooting potential issues.
How to disable dccp in rhel 8 – To disable DCIPP using `firewalld`, you must first identify the interface on which DCIPP is enabled. Then, you can remove the associated rules or create a new rule that explicitly denies traffic associated with DCIPP.
- Identify the interface(s): Use `firewall-cmd –get-active-zones` and `firewall-cmd –get-active-interfaces` commands to determine the active zones and interfaces.
- Disable rules: Use the `firewall-cmd –permanent –remove-service=dcpp` command to permanently remove the DCIPP service from the active zone. Ensure to reload the firewall rules using `firewall-cmd –reload`.
Iptables Configuration for DCIPP
The `iptables` tool offers a more granular level of control over network traffic, enabling customization beyond `firewalld`’s features. However, `iptables` requires a deeper understanding of network rules and proper configuration is crucial to avoid unintended consequences.
Disabling DCIPP with `iptables` involves the deletion of specific rules responsible for DCIPP traffic. This ensures that no DCIPP packets are forwarded or accepted.
- Identify the rules: Utilize `iptables -L` to examine the current ruleset and pinpoint the rules related to DCIPP.
- Remove rules: Execute `iptables -D INPUT -p tcp –dport 5000 -j ACCEPT` (or the appropriate command, depending on the specific rule). The example removes an inbound rule for TCP port 5000, but the actual port and protocol might vary.
- Save the changes: Save the new ruleset to persist them after a system reboot. This typically involves using `iptables-save > /etc/iptables.rules`.
- Reload the rules: Execute `iptables-restore < /etc/iptables.rules` to apply the saved rules.
Comparison of Methods
Both `firewalld` and `iptables` offer ways to disable DCIPP. However, `firewalld` is generally preferred for its user-friendliness and ease of management, especially for beginners. `iptables`, on the other hand, offers greater control, but requires a deeper understanding of networking concepts.
| Method | Description | Prerequisites |
|---|---|---|
| Firewalld | Simplifies DCIPP disabling through a service removal. | Basic familiarity with `firewalld` commands. |
| Iptables | Allows for precise control over DCIPP rules using command-line options. | Strong understanding of networking and `iptables` rules. |
Network Configuration Considerations
Disabling DCIPP (Data Center Bridging Protocol) on your RHEL 8 system might affect various aspects of your network configuration. Understanding which interfaces are involved and the potential consequences is crucial for a smooth transition. Careful consideration of network performance impacts and proper verification steps are necessary to avoid unexpected issues.
Identifying Affected Network Interfaces
DCIPP typically operates on specific network interfaces used for inter-datacenter communication. To identify these interfaces, review your network configuration files, particularly `/etc/sysconfig/network-scripts/ifcfg-*` files. Look for interfaces that have DCIPP-related parameters or labels in their configuration. These interfaces are the ones potentially affected by disabling DCIPP.
Impact on Network Performance
Disabling DCIPP can alter network performance depending on the setup. On LAN (Local Area Network) connections, the impact might be minimal if the communication is handled by other protocols. However, on WAN (Wide Area Network) connections where DCIPP plays a more prominent role, performance degradation could be observable, especially in high-bandwidth or latency-sensitive applications. Disabling DCIPP might lead to reduced efficiency in inter-datacenter communication.
Verifying Network Connectivity
After disabling DCIPP, thoroughly verify network connectivity. This involves testing communication between different network segments, both within the LAN and any connected WANs. Pinging or using other diagnostic tools are essential to ensure all network services and applications are functioning correctly. Failing to verify connectivity could lead to unforeseen issues or service disruptions.
Troubleshooting Connectivity Issues
If connectivity issues arise after disabling DCIPP, systematically troubleshoot the problem. First, check the configuration files (`/etc/sysconfig/network-scripts/ifcfg-*`) for any errors or inconsistencies. Second, review logs for any relevant error messages. Third, use network diagnostic tools like `ip`, `ping`, and `traceroute` to pinpoint the exact location of the problem. Detailed analysis and careful examination of network logs are vital for resolving connectivity problems.
Comparison of DCIPP Enabled/Disabled Effects
| Network Type | DCIPP Enabled | DCIPP Disabled | Impact |
|---|---|---|---|
| LAN | Potentially improves performance for specific applications | Minimal impact, potentially slight performance variation on specific applications. | Performance variation is likely minimal, but applications might experience changes in behavior. |
| WAN | Potentially improves performance for inter-datacenter communication | Significant performance reduction in inter-datacenter communication. | Reduced inter-datacenter communication speed, requiring alternative protocols for these communications. |
System Impact Analysis
Disabling Data Center Connectivity Protocol (DCIPP) on Red Hat Enterprise Linux 8 can have significant implications for system stability, security, and network performance. Understanding these potential impacts is crucial before making any decisions about disabling DCIPP. This section delves into the potential consequences and provides a framework for evaluating the trade-offs.
Potential System-Level Consequences
Disabling DCIPP might lead to issues in scenarios where network topology changes frequently or in environments with dynamic routing protocols. For instance, if a network device or server is added or removed, DCIPP can automatically adjust routing tables, ensuring seamless communication. Without DCIPP, manual intervention or alternative configuration might be required, potentially causing delays or network outages during transitions. Moreover, if DCIPP is disabled, applications relying on its functionality might exhibit unexpected behavior.
Security Implications of Disabling DCIPP
Disabling DCIPP removes a layer of automated network protection. While DCIPP itself doesn’t directly address security vulnerabilities, its presence helps maintain network integrity, which indirectly contributes to overall security. Without it, the system becomes more susceptible to configuration errors or malicious actors exploiting network instability. Incorrect manual configurations can introduce security flaws, making the system more vulnerable.
Conflicts with Other Network Services or Applications
Some network services and applications might rely on DCIPP for proper functioning. For instance, certain virtualized environments or containerized applications could encounter issues. The absence of DCIPP’s automatic routing updates might cause unexpected delays or failures in these services. Thorough investigation of potential conflicts with existing network infrastructure and applications is crucial before disabling DCIPP.
Potential Performance Issues or Benefits
The impact on performance is not straightforward. In some cases, disabling DCIPP might improve performance by eliminating unnecessary overhead from constant updates. However, in scenarios involving frequent network topology changes, performance could be negatively impacted due to the need for manual adjustments or the lack of automatic adaptation. It is important to consider the specific network environment and workload when evaluating the potential performance impact.
Impact Analysis Table
| Feature | Enabled DCIPP | Disabled DCIPP | Impact |
|---|---|---|---|
| Network Stability | High; automatic adaptation to changes | Low; requires manual intervention for changes | Potentially higher risk of network outages during transitions, especially in dynamic environments |
| Security | Indirectly enhances security by maintaining network integrity | Lower level of protection; more vulnerable to misconfigurations or attacks exploiting network instability | Increased risk of security breaches due to potential misconfigurations |
| Performance | Potentially slightly reduced performance due to overhead of updates | Potentially improved performance in stable environments, but could be degraded in dynamic ones | Performance is dependent on network environment and frequency of changes |
| Application Compatibility | High compatibility with applications designed for dynamically changing networks | Potential incompatibility with applications relying on DCIPP for proper functioning | Compatibility issues are likely if applications are not explicitly designed to handle manual configuration. |
Troubleshooting and Remediation
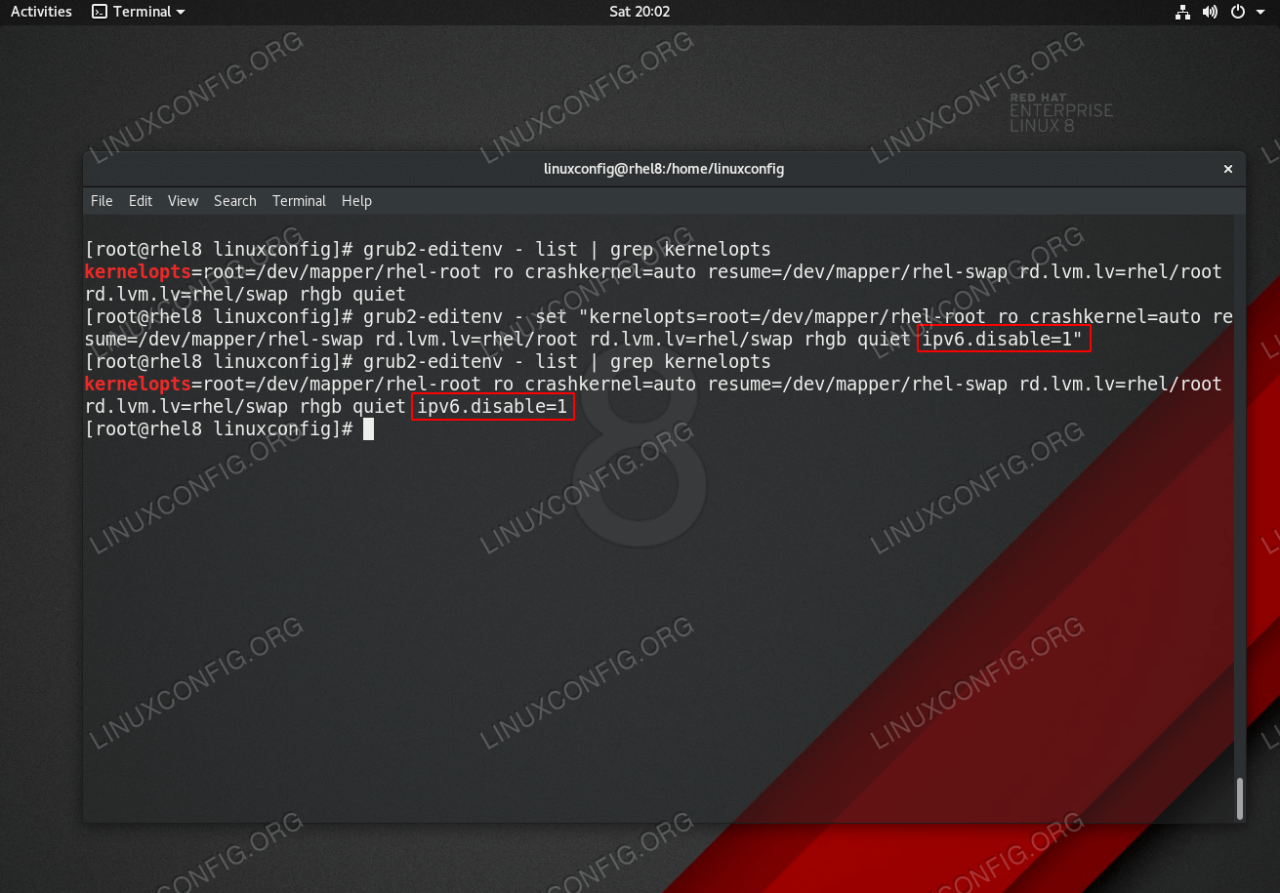
Disabling DCIPP (Datagram Congestion Control Protocol) on RHEL 8 systems can potentially lead to network connectivity issues. This section details methods for diagnosing and resolving such problems, as well as the process for restoring DCIPP if needed. Understanding the potential causes and appropriate troubleshooting steps is crucial for maintaining network stability.
Diagnosing Connectivity Issues
After disabling DCIPP, meticulously monitor network performance. Common symptoms of connectivity problems include slow download and upload speeds, intermittent connectivity drops, or complete network inaccessibility. Tools like `ping`, `traceroute`, and `netstat` can be employed to diagnose network issues. These tools provide valuable insights into network latency, packet loss, and routing problems. Detailed logging of network activity using system logs and network monitoring tools is vital for identifying patterns and root causes.
Potential Solutions for Connectivity Problems
Several factors can contribute to connectivity issues after DCIPP disablement. Addressing network configuration mismatches, verifying sufficient network resources, and investigating potential conflicts with other network services are crucial steps in resolving these problems. Troubleshooting involves systematically checking network settings, firewall rules, and the configurations of related services. If network resource constraints are suspected, upgrading or optimizing network infrastructure might be necessary.
Troubleshooting Examples
Several scenarios can lead to connectivity problems after disabling DCIPP. For instance, if `ping` requests consistently time out, it suggests a problem with network reachability or routing. Analyzing the output of `traceroute` can reveal the point of failure in the network path. If download speeds are significantly slower than expected, examining network bandwidth usage and other network traffic may pinpoint the bottleneck. Detailed logs of network events are crucial in pinpointing the source of the problem.
Reverting the Disabling of DCIPP
Re-enabling DCIPP is essential for restoring network functionality to its original state. Failure to reinstate DCIPP might result in persistent network problems. Following the correct procedure for re-enabling DCIPP is crucial to ensure proper network operation.
Restoring DCIPP – Step-by-Step Guide
Restoring DCIPP involves reversing the steps taken to disable it. This involves the same configuration files and commands. The process is Artikeld below:
- Identify the method used to disable DCIPP. This is critical for accurate restoration.
- Use the corresponding method to re-enable DCIPP, reversing the previous steps.
- Verify the re-enabled setting through the appropriate command or configuration file.
- Check for any lingering network issues or conflicts.
- Monitor network performance for a period to confirm the restoration of normal functionality.
Best Practices and Recommendations: How To Disable Dccp In Rhel 8
Disabling Data Center Connectivity Protocol (DCIPP) in Red Hat Enterprise Linux 8 (RHEL 8) requires careful consideration of network environment, potential impacts, and alternative solutions. This section provides guidelines for making informed decisions regarding DCIPP disablement.
Disabling DCIPP should only be performed when thoroughly understanding its role in your network infrastructure and potential consequences. Improper disablement could lead to unexpected issues, including reduced network performance or security vulnerabilities.
Guidelines for Disabling DCIPP in RHEL 8
Careful planning and evaluation are crucial before disabling DCIPP. Consider the specific needs of your network and weigh the potential benefits against the risks. Documentation of the existing network configuration and the impact of DCIPP is highly recommended.
Considerations for Different Network Environments
The suitability of DCIPP disablement varies significantly based on the network topology and application deployments. A simple LAN environment might not necessitate DCIPP disablement, while a complex, multi-site environment might benefit from its removal.
Situations When to Disable DCIPP
Disabling DCIPP is sometimes necessary if it interferes with other network services or causes instability. For example, if DCIPP conflicts with firewall rules or causes performance degradation, disabling it could resolve these issues. Thorough analysis is vital before making this decision.
Situations When Disabling DCIPP Might Be Unnecessary
In many scenarios, disabling DCIPP may not be required. If DCIPP is functioning correctly and not impacting network performance or stability, there is no need to disable it. Careful monitoring and evaluation are key to determining the optimal course of action.
Key Considerations Before Disabling DCIPP
- Verify DCIPP functionality: Ensure that DCIPP is causing the specific issues you’re trying to resolve. Tools for monitoring network traffic and identifying potential conflicts should be used.
- Identify alternative solutions: Exploring other solutions to address the problem is crucial. Solutions like optimizing network configurations or upgrading hardware might be more effective than disabling DCIPP.
- Document existing configurations: Comprehensive documentation of the current network setup, including IP addresses, routing tables, and network services, is vital for troubleshooting and future reference.
- Analyze potential impact: Thoroughly assess the potential impact of disabling DCIPP on network performance, security, and existing applications. Testing in a non-production environment is recommended.
- Seek expert advice: Consulting with network administrators or specialists familiar with DCIPP and your specific network configuration is recommended.
- Implement thorough testing: A trial run in a non-production environment, before implementing the changes in a live production environment, is essential to identify potential issues before impacting users.
FAQ Insights
What are the potential security implications of disabling DCIPP?
Disabling DCIPP might expose your network to certain security risks, particularly if not properly managed. It’s crucial to thoroughly assess the security posture of your network after disabling DCIPP and take appropriate countermeasures.
How can I verify network connectivity after disabling DCIPP?
Use tools like ping, traceroute, and netstat to confirm connectivity to key network resources. Thorough testing across different network segments is recommended.
Are there any conflicts with other network services when disabling DCIPP?
There might be potential conflicts with other network services or applications. Thorough testing and monitoring are crucial to identify and resolve any conflicts.
What are the prerequisites for using different methods to disable DCIPP?
The prerequisites will vary based on the chosen method. Ensure you have necessary administrative privileges and understand the specific requirements for each method before proceeding.